Example Setup Using OneLogin
Introduction
OneLogin is a cloud-based identity and access management provider. This document describes how to integrate OneLogin as an identity provider (IdP) by configuring OpenID Connect (OIDC). See OneLogin for details about the service.
| At the moment, ownCloud clients don’t work with OneLogin as IdP which is a known issue. |
Setup and Configuration
The sections below will explain these areas and provide configuration examples using OneLogin as the external Identity Provider.
Configure OneLogin
Follow these steps to configure OneLogin for use with OpenID Connect (OIDC):
-
Login to OneLogin via your domain login
https://<yourdomain>.onelogin.com/admin2. -
Go to to manage the registered applications.
-
Click on Add App in the upper right corner.
-
Search for
openidand select theOpenId Connect (OIDC)app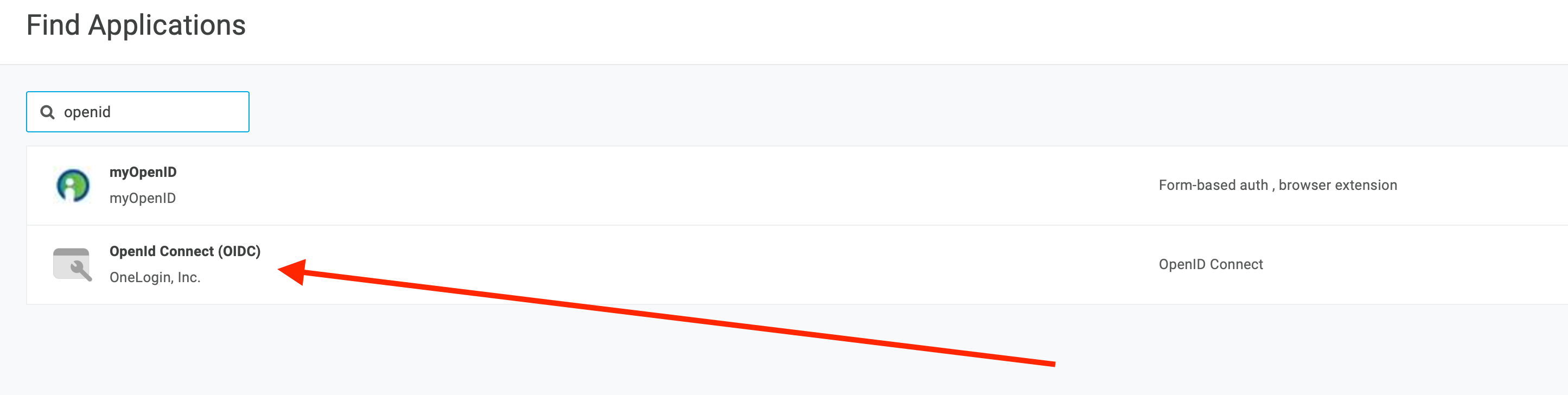
-
Provide a name and configure images if needed.
-
Hit Save
-
Go to Configuration and enter values for
Login Urlwhich points to you system and theRedirect URI’s, which is the url of you system followed by/index.php/apps/openidconnect/redirect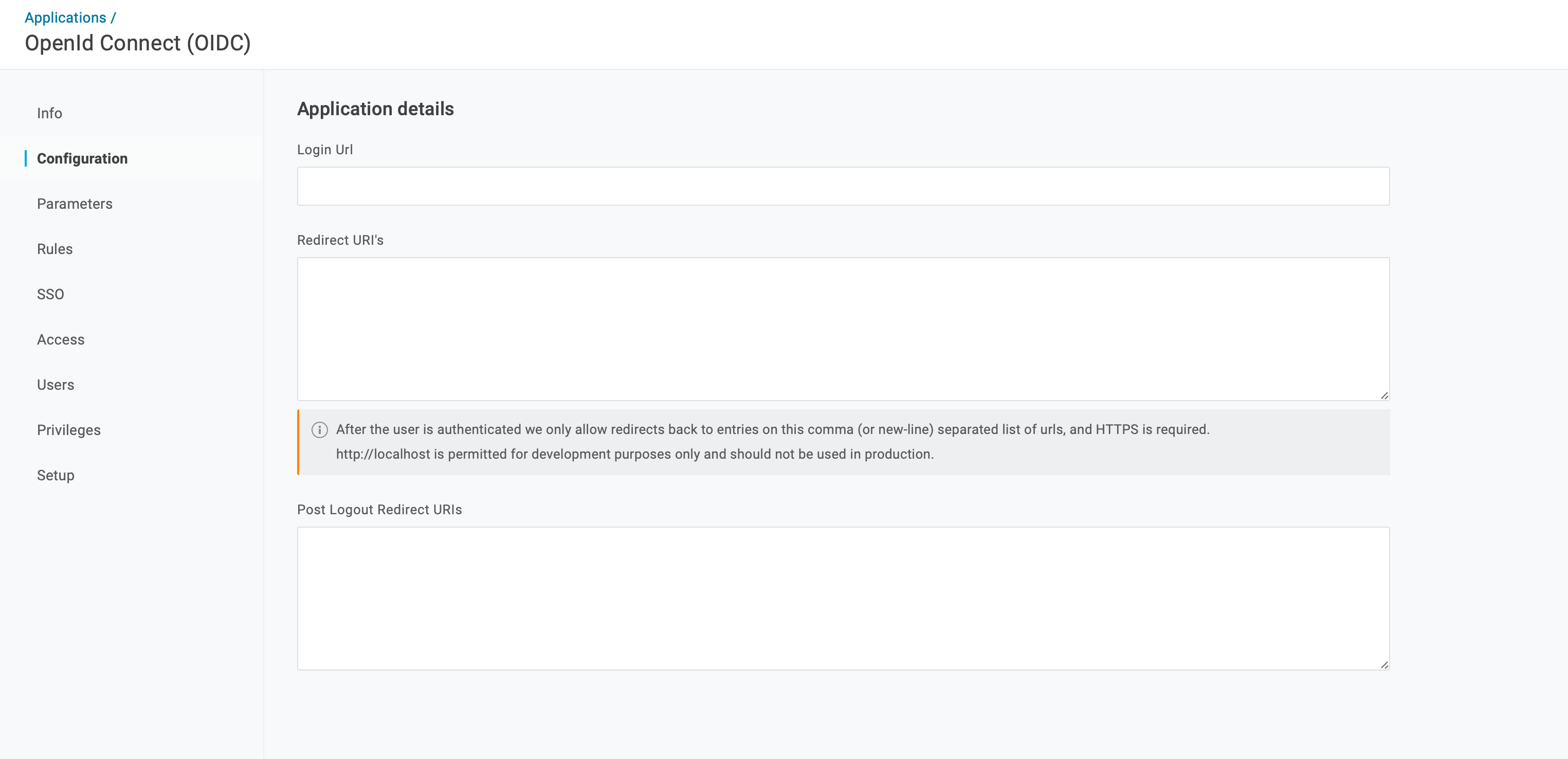
-
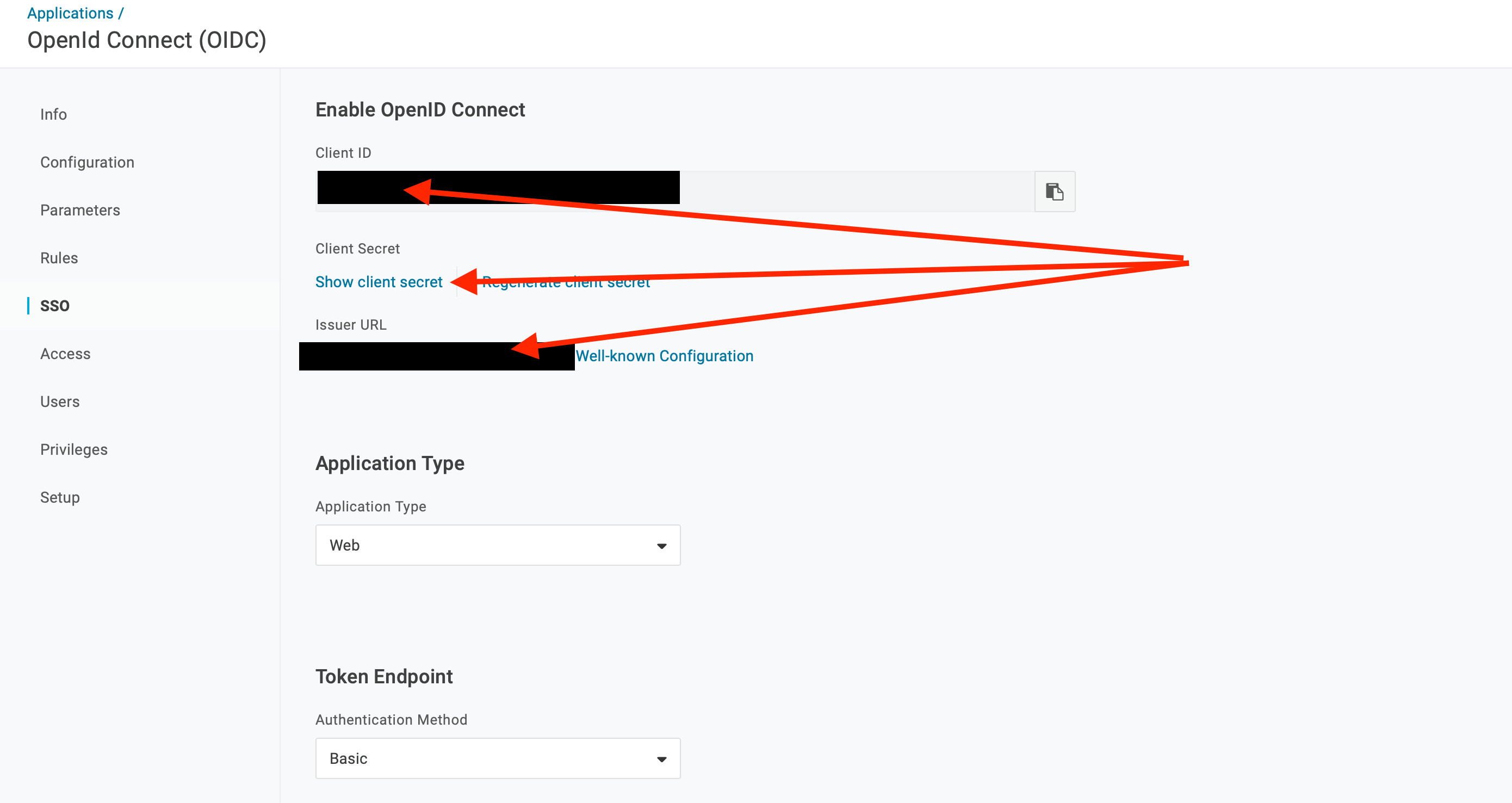
Go to SSO and note the values for Client ID, Client Secret and Issuer URL for later use.
Configure ownCloud Server
These are the generic steps to set up ownCloud Server to work with OpenID Connect, for details see the sections below:
-
Install the OpenID Connect App.
-
Configure
config.php. -
Set up service discovery.
| It is recommended to first figure out all configurations on a test system and to bring it to the production system once it’s proven to work. Enabling the OpenID Connect App on the production system should be the last step in this process as it will then advertise OpenID Connect to all clients. |
List of OpenID Connect config.php Parameters
Follow this link to read more about the OIDC config.php parameters available to configure OpenID Connect on ownCloud Server.
Example config.php Setup
An example snippet that can be added to config.php is shown below. You need to add both config values as listed below. The example expects that login users have already been created in ownCloud.
Use these links to see the corresponding configuration section for:
'http.cookie.samesite' => 'None',
'openid-connect' => [
'auto-provision' => ['enabled' => false],
'provider-url' => 'YOUR-ISSUER-URL',
'client-id' => 'YOUR-CLIENT-ID',
'client-secret' => 'YOUR-CLIENT-SECRET',
'loginButtonName' => 'OneLogin',
'autoRedirectOnLoginPage' => false,
'mode' => 'email',
'scopes' => [],
'use-access-token-payload-for-user-info' => false,
],If you want to let ownCloud create users which are not present during a OIDC authentication, replace
'auto-provision' ⇒ ['enabled' ⇒ false], with:
'auto-provision' => [
'enabled' => true,
'email-claim' => 'email',
'display-name-claim' => 'name',
],Service Discovery Setup
For details see Set Up Service Discovery.